Raspberry Pi Security Guide: Open Ports, Firewalls & More!
Are you ready to transform your Raspberry Pi into a fortress, shielding it from the digital onslaught? Securing your Raspberry Pi is not just a recommendation; it's a fundamental necessity in today's interconnected world, ensuring your projects and data remain safe from prying eyes and malicious actors.
Setting up a new Raspberry Pi computer can be an exciting endeavor, opening doors to countless possibilities. However, before diving into projects, it's crucial to prioritize its security posture. This involves closing any unnecessary open ports and establishing a robust firewall to regulate incoming connections. This proactive approach is the first line of defense against potential network attacks.
To effectively navigate the landscape of Raspberry Pi security, it's important to understand the tools and techniques at your disposal. One of the primary methods is to install and configure a firewall. The firewall acts as a gatekeeper, meticulously examining all incoming and outgoing network traffic, blocking any suspicious or unauthorized connections.
- Greg Gutfeld Is He Gay Sexuality Partner Explored
- Lattos Parents Misti Pitts Shayne Stephens Untold Story
Let's delve into the steps needed to secure your Raspberry Pi, from the initial setup to ongoing maintenance. We'll cover critical aspects such as choosing the right firewall, opening specific ports for essential services, and regularly checking for vulnerabilities. By the end of this guide, you'll have a solid understanding of how to fortify your Raspberry Pi and keep your digital projects safe.
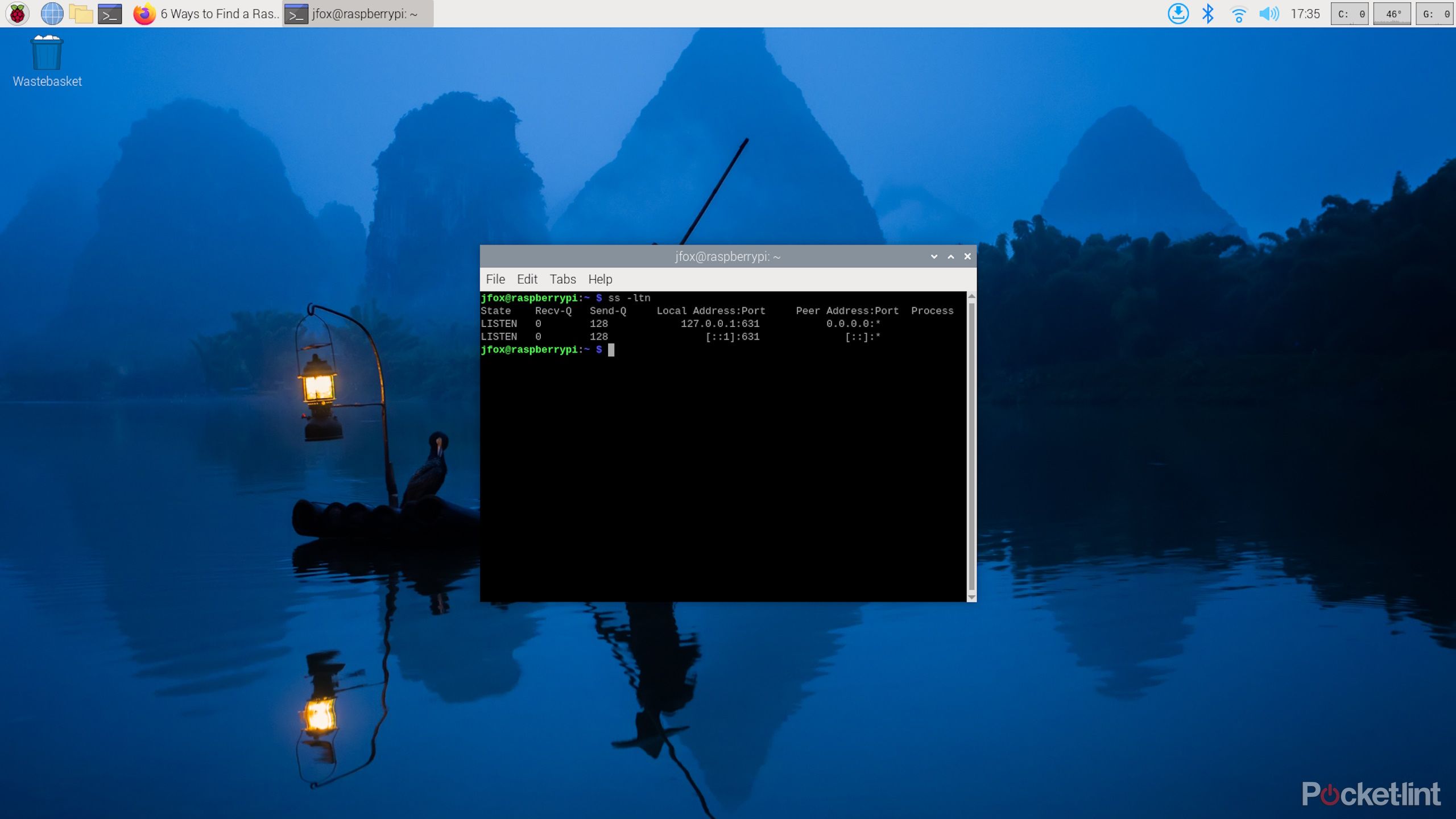
To start, let's explore the concept of open ports. Think of ports as doorways into your Raspberry Pi. Each port is associated with a specific service or application. For example, port 22 is typically used for Secure Shell (SSH) connections, allowing you to remotely access and manage your Pi. Port 80 is commonly associated with web servers. Having too many open ports can be a security risk, as they create potential entry points for attackers.
In order to keep your device safe, you should consider a firewall. A firewall, such as the popular and user-friendly "ufw" (Uncomplicated Firewall), acts as a barrier, meticulously scrutinizing all incoming and outgoing network traffic, only allowing authorized connections.
- Lisabeth Shatner Bio Net Worth William Shatners Daughter
- Jiwon4u Tiktok Aegyo More See Her Latest Content Now
Before diving into the intricacies of securing your Raspberry Pi, let's gather some essential information about the device and the owner of the setup, so its easier to understand and setup.
| Category | Details |
|---|---|
| Device | Raspberry Pi (Model Number and Revision, e.g., Raspberry Pi 4 Model B) |
| Operating System | Raspberry Pi OS (formerly Raspbian), specifying the version (e.g., Bookworm, Bullseye) |
| IP Address | Static or Dynamic IP Address (Important for port forwarding) |
| Firewall (if installed) | ufw (Uncomplicated Firewall) - a popular choice; iptables (older systems); nftables (newer systems) |
| Internet Connection | Wired Ethernet or Wireless (Wi-Fi), and any VPN configuration |
| Router Model | Make and model of the router (for port forwarding configuration) |
| Basic Setup | Whether you have set up the device from the graphical interface or console. |
| Serial Port Usage | Whether the device uses the universal asynchronous receiver/transmitter protocol, or uart. |
| USB Devices | Connected devices, i.e. usb microphone and speaker. |
| Usernames and Passwords | Ensure usernames and passwords are secure. |
| Reference Website | Raspberry Pi Official Website |
The serial port (UART), often referenced on Raspberry Pi devices, allows communication between connected devices. This communication method is widely used in numerous projects. On Raspberry Pi OS, the serial port (UART) can be enabled through the graphical interface or command lines within the terminal. Its crucial to configure the serial port correctly to interface with hardware components.
Now, let's move into the critical steps to safeguard your Raspberry Pi. First, we'll explore the importance of closing unnecessary ports. A core principle of security is to limit the attack surface. Every open port is a potential vulnerability. Identify which services you genuinely need and close the rest. Use tools like 'netstat' or 'ss' to see what ports are open and listening. Close ports that aren't essential.
Once you've closed all unnecessary ports, the next essential step is to choose and configure a firewall. For simplicity, ufw (Uncomplicated Firewall) is a great choice, and it is often pre-installed or easily installed. It is easy to use and provides a user-friendly interface for managing firewall rules. On older Raspberry Pi systems based on Debian 9 (Stretch), iptables is the default firewall, while on newer systems based on Debian 10 (Buster) and newer, nftables is the default. However, ufw provides a simplified way to configure either iptables or nftables in the background, making it a preferred option.
To install ufw on your Raspberry Pi, use the following command: sudo apt update; sudo apt install ufw. Once installed, you can configure it through the command line. The command 'ufw enable' activates the firewall, protecting your system. However, before enabling ufw, you should establish your firewall rules. This involves allowing only the specific ports that are required for your applications and services to function.
Now, let's discuss how to manage your Firewall. Your firewall rules are crucial for managing network traffic. You can allow connections through the firewall with commands such as 'sudo ufw allow 22' to open port 22 for SSH. To disable the firewall, you can use 'sudo ufw disable'. Its very important to check the status of the firewall using 'sudo ufw status'. This will show you which ports are open and the overall status of the firewall.
Here's a practical guide on how to set up a firewall with ufw on your Raspberry Pi:
- Installation and Activation: Begin by installing the Uncomplicated Firewall (ufw). Update the package lists and then install ufw by typing sudo apt update and sudo apt install ufw. After installation, enable the firewall with sudo ufw enable. This command activates the firewall, which immediately starts blocking incoming connections that aren't explicitly allowed.
- Allow SSH (Important): To permit remote access, allow SSH connections using the command sudo ufw allow ssh or sudo ufw allow 22. This opens port 22, enabling you to connect to your Raspberry Pi remotely. It's an essential step if you intend to manage your Pi over the network.
- Allow Other Services: Allow services such as HTTP (port 80) and HTTPS (port 443) if you are hosting a web server. Use the commands sudo ufw allow 80 and sudo ufw allow 443, respectively.
- Open UDP Ports: If your application needs UDP connections, for example, for services such as DNS or NTP, open the respective ports. For example, to allow UDP port 53 (DNS), use sudo ufw allow 53/udp.
- Default Deny: Set the default policies to deny incoming connections and allow outgoing connections. This ensures that only the traffic you explicitly allow is permitted. Use sudo ufw default deny incoming and sudo ufw default allow outgoing.
- Check the Status: Verify the status of your firewall with sudo ufw status. This command displays all active rules and their status, giving you a quick overview of your firewall's configuration.
- Testing Your Setup: Test your setup to verify the firewalls functionality. Try to access your Raspberry Pi from another device and verify that the allowed ports are working as expected and others are blocked.
To reach your Raspberry Pi from outside your local network, you will need to configure port forwarding on your router. This tells your router to send incoming traffic on specific ports to the Raspberry Pi's internal IP address. The exact steps vary depending on your router's make and model, but generally involve accessing your router's configuration page via a web browser and finding the port forwarding settings. Remember to forward port 80 and 443 if you intend to host a web server.
If you are using a VPN, it adds an extra layer of security by encrypting your internet traffic and masking your IP address. It's advisable to configure your Raspberry Pi to connect to a VPN before opening any ports, as the VPN will route your traffic securely through the internet. If your VPN service uses specific ports, make sure these are permitted through the firewall. The most important thing is to ensure that your VPN is active and correctly configured.
For those who want to test an open UDP port, here's how you can do so:
Check if you need a UDP port. Determine whether your application or service needs a UDP port. UDP is a connectionless protocol, often used for streaming media, online gaming, and other real-time applications where speed is crucial, and packet loss is acceptable.
Configure UFW to allow the port. You can allow UDP traffic through the firewall, the command is sudo ufw allow /udp. Replace `` with the UDP port number you need. For instance, if you're setting up a DNS server, you might allow port 53/udp.
Verify the rule with sudo ufw status, you will check that the rule has been successfully applied to allow incoming UDP traffic on the specified port.
Test the connection. You can verify that the UDP port is open and listening by using tools like netcat (nc) or a port scanner from another machine on the network or from the internet.
Securing your Raspberry Pi is not a one-time task. It's an ongoing process that involves keeping your software updated. Raspberry Pi OS and other software packages are regularly updated with security patches. Keeping your software updated is the best way to prevent vulnerabilities. Use the command 'sudo apt update' to refresh the package lists and 'sudo apt upgrade' to install any available updates. It is an essential task for system security.
Regularly audit your system and check logs. Reviewing your system logs is a crucial part of maintaining the security of your Raspberry Pi. These logs record events that can provide insights into any potential security breaches or suspicious activities. Learn where the logs are stored on your system. Common log files include '/var/log/auth.log' (authentication logs) and '/var/log/syslog' (system logs). Examine the contents to identify unusual login attempts, failed access attempts, or any unauthorized activity.
Moreover, perform periodic vulnerability assessments. Regularly checking your system for potential security vulnerabilities can help you discover weaknesses before attackers can exploit them. There are tools that can automate this process. They scan your system for known vulnerabilities and provide recommendations for remediation. These scans will assist in ensuring your Raspberry Pi remains secure.
Here are additional tips for securing your Raspberry Pi:
Change the default password: One of the first steps should be changing the default password for the "pi" user. This is a fundamental security measure.
Disable unnecessary services: Any unused services or applications can be disabled to reduce the attack surface. This can be done through the system configuration.
Configure SSH securely: If using SSH, configure it securely by changing the default port (port 22), disabling password authentication, and using key-based authentication instead.
Monitor network traffic: Utilize network monitoring tools to identify any suspicious activity or unusual network traffic. These tools can help detect any possible attacks.
Isolate your Pi: If possible, keep your Raspberry Pi on a separate VLAN or network segment to limit its exposure to other devices on your network.
Enable two-factor authentication: Enable two-factor authentication for services like SSH and any web applications. This enhances security by requiring a second verification method.
Regularly back up your data: Maintain regular backups of your data. This will help you restore the system in case of a security breach.
Troubleshooting is part of any security process. The most common issue is the inability to connect. Here's how to approach troubleshooting if you can't connect remotely to your Raspberry Pi after opening ports:
Check the Basics: Double-check the Raspberry Pi's IP address and make sure your device is on the same network. Verify the network cable connection or the Wi-Fi connection status.
Firewall Rules: Confirm that the firewall allows traffic on the correct port. Use the command 'sudo ufw status' to view the status of your firewall and ensure the necessary ports are open.
Port Forwarding: Ensure port forwarding is configured correctly on your router. The internal IP address should match your Raspberry Pi's and you must be sure that the ports are forwarded.
VPN Conflicts: Check if a VPN is interfering with your connection. If you use a VPN, make sure it is configured correctly and allows connections to your Raspberry Pis ports.
Service Status: Check the status of the service youre trying to access. For example, ensure SSH is running by typing `sudo systemctl status ssh`.
Test with Port Scanners: Use a port scanner from another device to verify that the port is open and accessible.
Router Configuration: Verify your routers firewall settings aren't blocking the connection. Some routers have default settings that can block incoming traffic.
Check Logs: Review system logs for any error messages that may provide clues to the problem. Log files like `/var/log/auth.log` and `/var/log/syslog` are helpful.
Securing a Raspberry Pi requires a proactive approach, involving various security measures. By implementing these steps, you can significantly improve the security of your Raspberry Pi and reduce the risks of unauthorized access and cyber threats. Regularly audit and assess your system, keep software updated, and maintain a cautious approach to your network configuration.
- Chance Combs Honors Mother Sweet Birthday Tributes Photos
- Kirstentoosweet Leaks Unveiling The Truth More
9 must know Raspberry Pi tips and tricks

Raspberry Pi 3 Raspbian Open Port Or Make My Webapp

How to check open ports on Raspberry Pi Linux Tutorials Learn Linux